Single sign-on (SSO) via Okta
If you have Okta as your identity provider (IdP), you can use it to log in to your Nolt board using our single sign-on mechanism. This provides seamless experience for your users by eliminating the need for them to create a separate account in Nolt. Nolt supports Single-sign-on using SAML 2.0 and OpenID Connect protocol and you can configure either protocol to enable SSO. This comprehensive guide will help you to setup Okta as your SSO provider for Nolt.
Table of Contents
OpenID Connect (OIDC) Integration
If you want to use OpenID Connect based authentication for your users then you can follow along the steps to integrate Okta with Nolt.
1. Setting up Application in Okta
Sign in to your Okta account as an administrator. Navigate to Applications → Applications → Create App Integration. A pop-up screen to setup a new application will appear. Select OIDC - OpenID Connect as the sign-in method and Web Application as the application type.
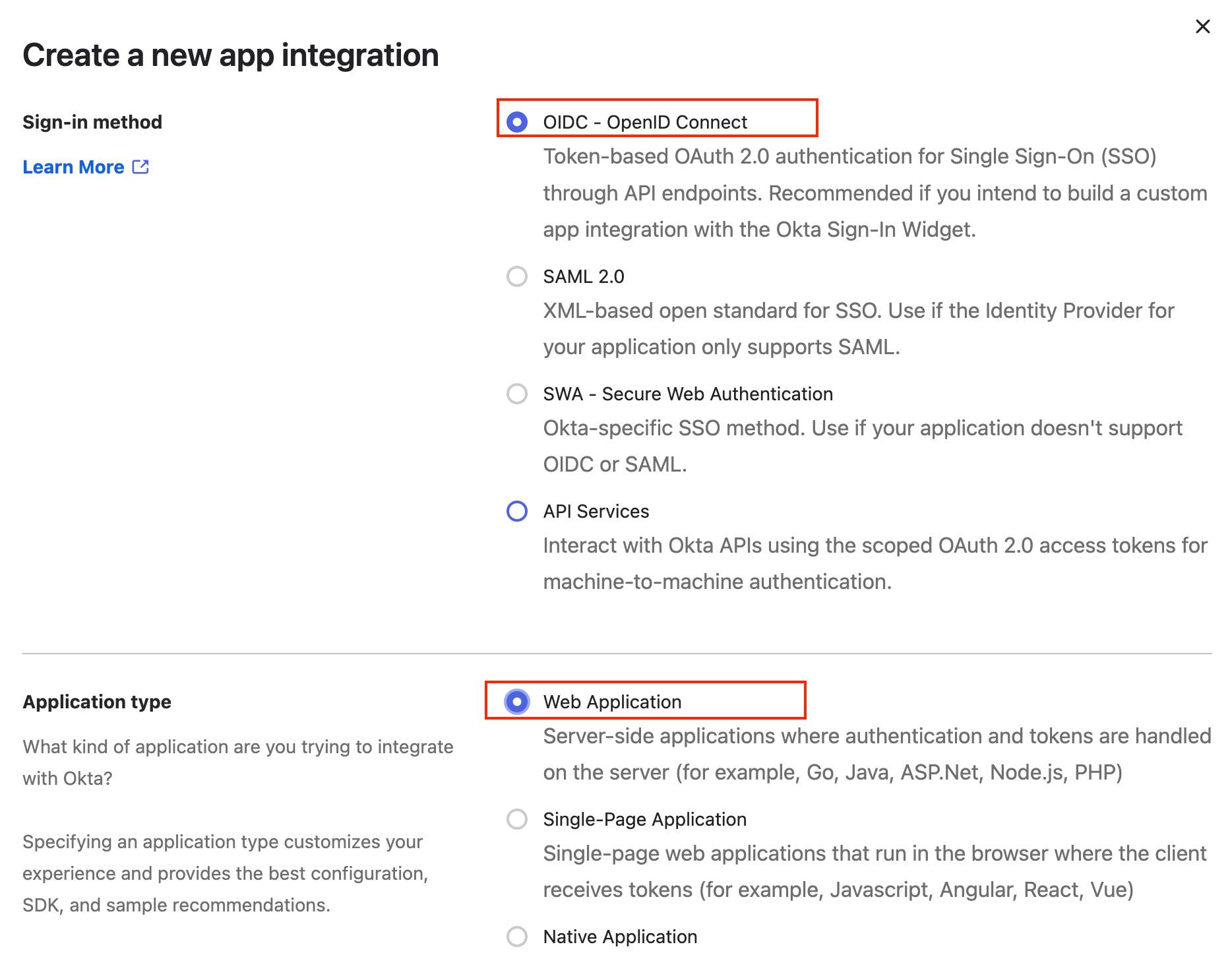
Use the following settings for configuring the application:
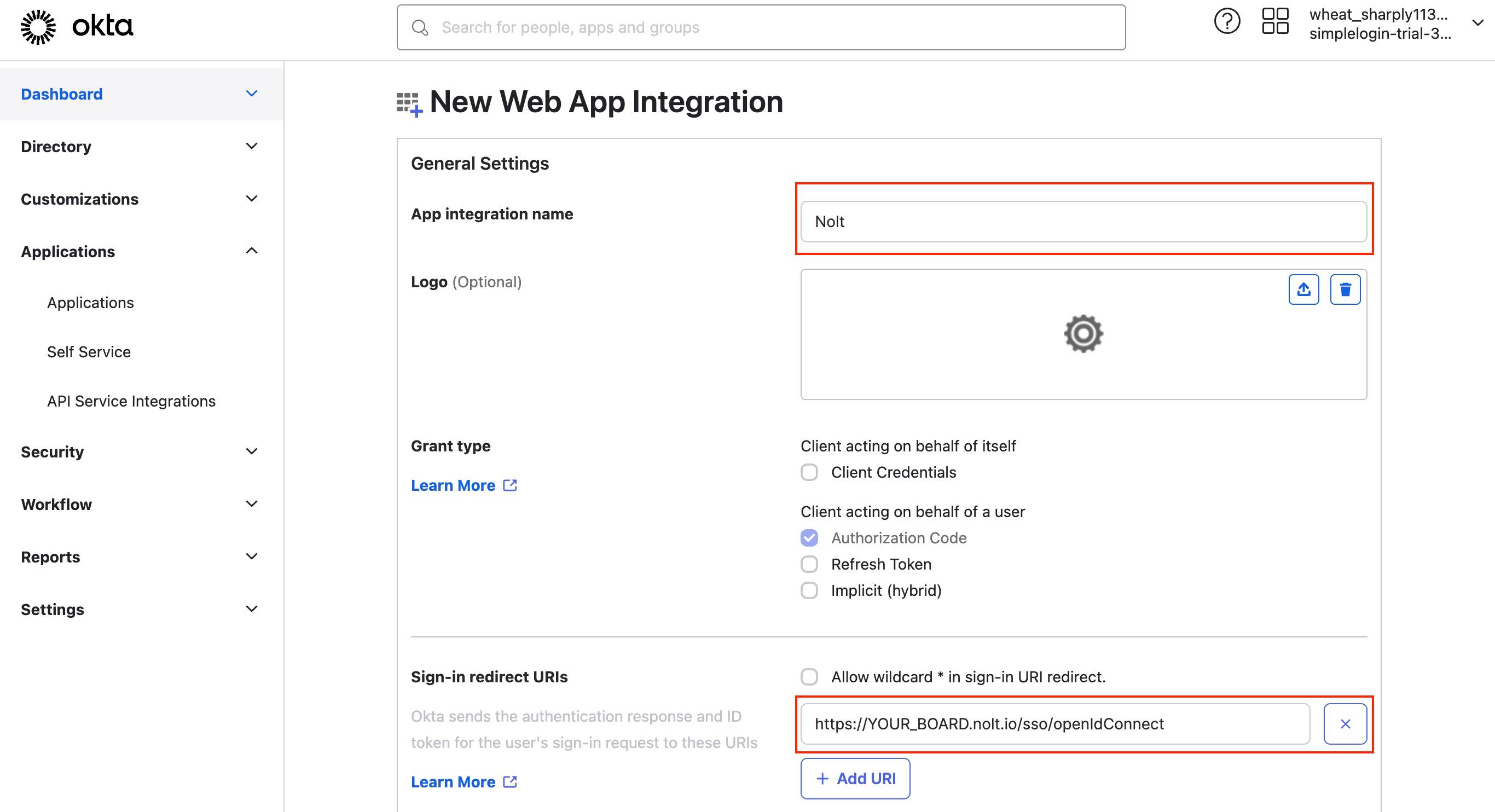
- Name the app Nolt and upload your logoYou can name app as your preferred name and upload your logo.
- Sign-in redirect URIs:
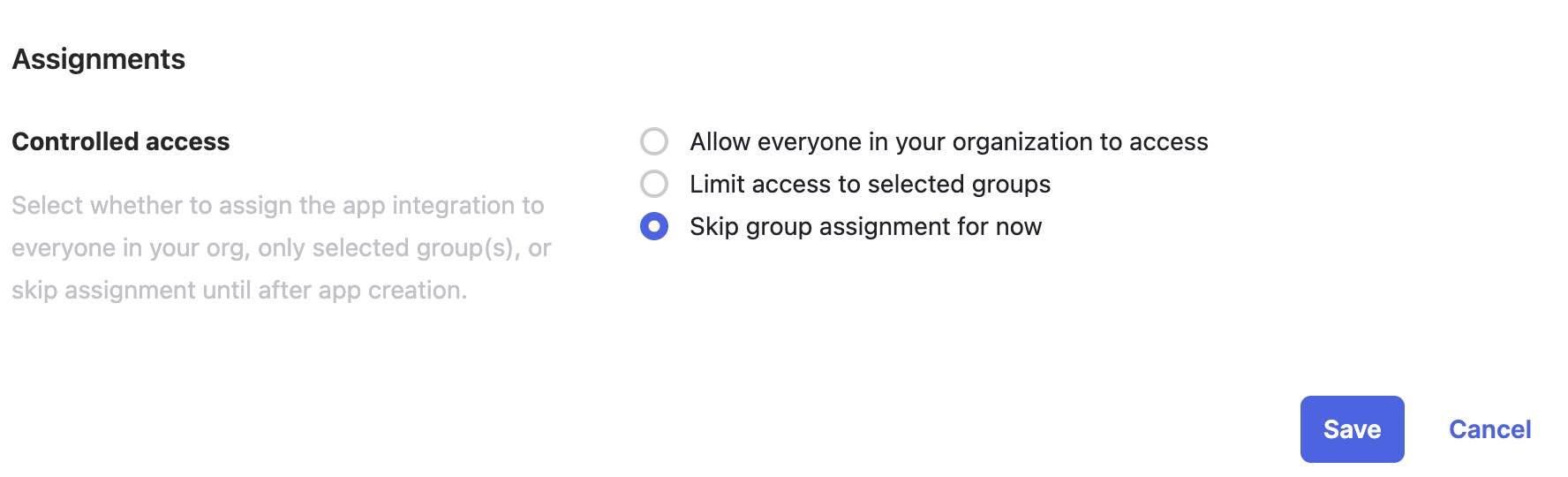
https://YOUR_BOARD.nolt.io/sso/openIdConnect - AssignmentsSelect your preferred assignment of users in your organization.
- Save the application
2. Integrating in Nolt
Navigate to your board → Integrations → OpenID Connect. Set up all the required fields to activate the integration.
- Client ID:Copy the Client ID from the Okta OIDC application.
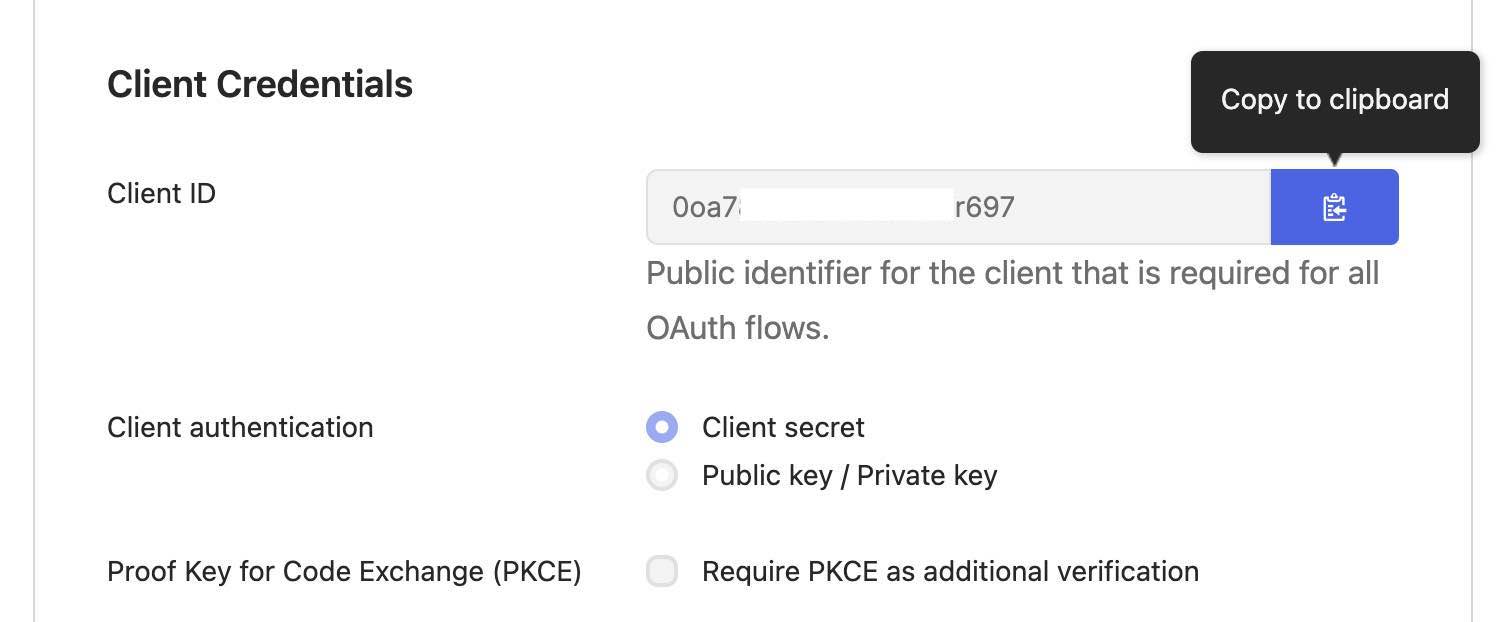
- Client Secret:Copy the Client Secret from the Okta OIDC application.
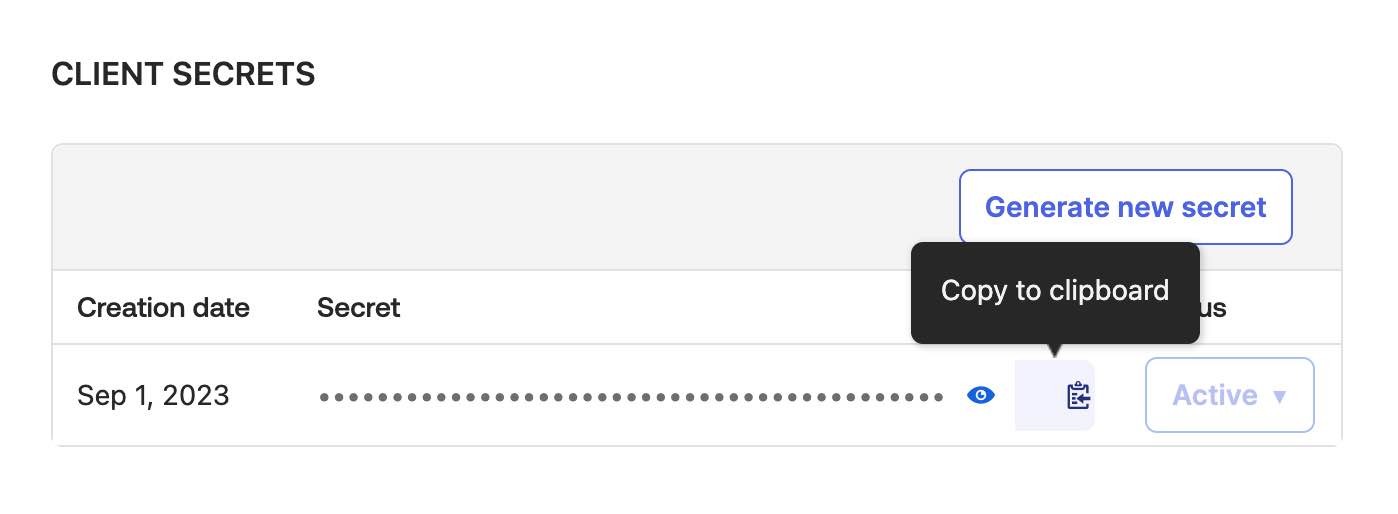
Note: To get Client ID and Client Secret, navigate to Applications → Nolt → General in Okta.
- Issuer URL:
https://YOUR_OKTA_DOMAIN.okta.com/oauth2/default - Token URL:
https://YOUR_OKTA_DOMAIN.okta.com/oauth2/default/v1/token - Remote Login URL:
https://YOUR_OKTA_DOMAIN.okta.com/oauth2/default/v1/authorize?client_id=CLIENT_ID&response_type=code&scope=openid%20profile%20email&redirect_uri=https://YOUR_BOARD.nolt.io/sso/openIdConnect&state=randomstate - Remote logout URL (optional)Add a Remote logout URL if you want to redirect users to a specific URL after they log out from their Nolt account.
- User role structure (optional)If you are passing the user role for nolt other than noltUserRole in the OIDC token, you need to set this field. If you have the attribute as follows:Then the user role structure should be set as follows:
userRole: 'ADMIN'userRole - Custom Attributes (optional)If you are passing any custom attributes in OIDC token, you need to set this field. If you have custom attribute as follows:Then the user custom attribute structure should be set as follows:
department empId{"Department":"department","EmployeeID":"empId"} - Click Test and activate:This should activate the SSO. To test the SSO try logging in as a new user.
Note: YOUR_OKTA_DOMAIN is available in the url of your Okta organization. Make sure to replace YOUR_OKTA_DOMAIN, CLIENT_ID and YOUR_BOARD before using the remote login URL.
SAML 2.0 Integration
If you want to use SAML 2.0 based authentication for your users then you can follow along the steps to integrate Okta with Nolt.
1. Setting up Application in Okta
Sign in to your Okta account as an administrator. Navigate to Applications → Applications → Create App Integration. A pop-up screen to setup a new application will be shown. Select SAML 2.0 as the sign-in method and name the app Nolt and upload your logo..
2. SAML settings
Use the following settings for configuring SAML:
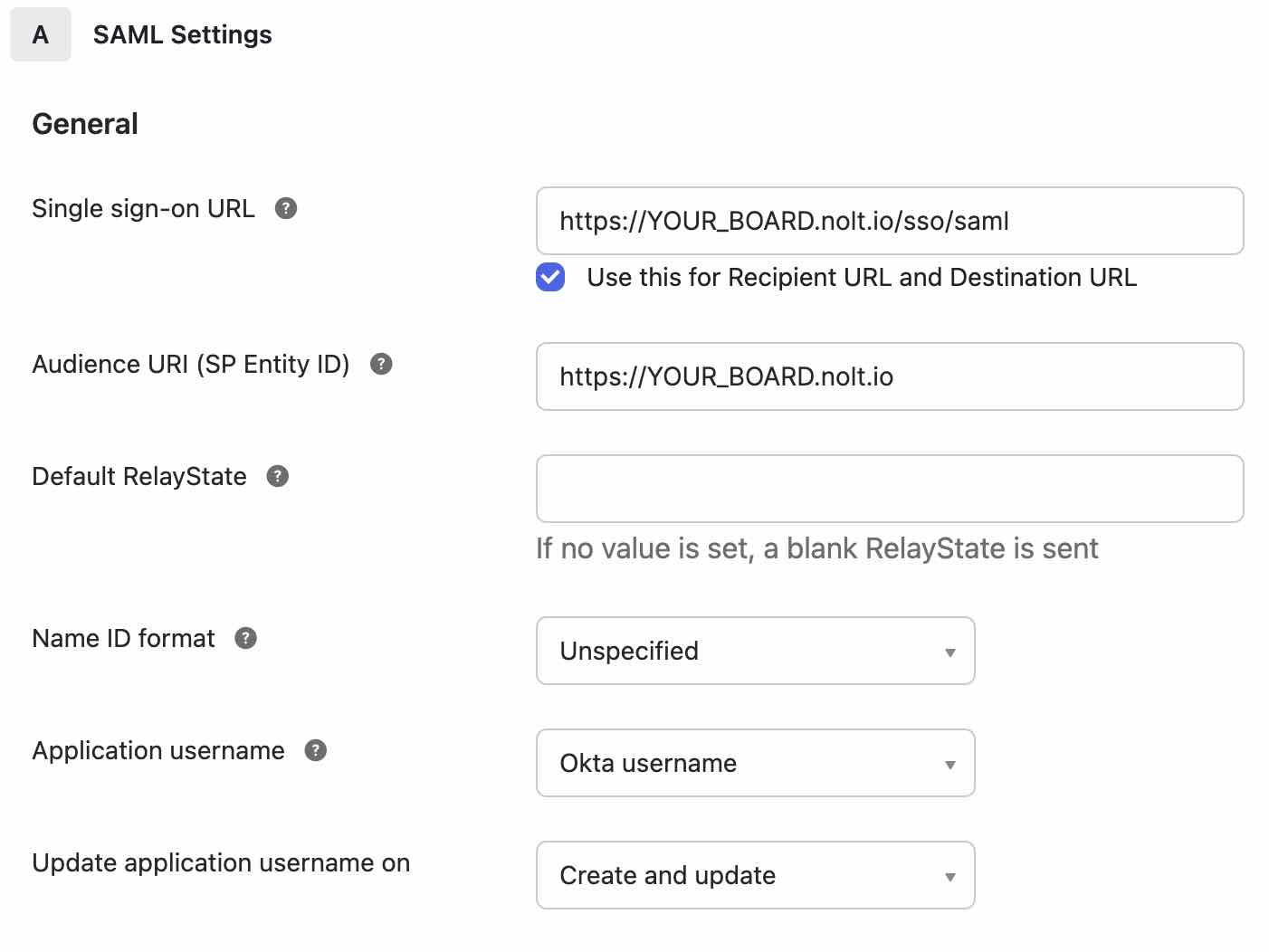
- Single sign-on URL:
https://YOUR_BOARD.nolt.io/sso/samlLeave the 'Use this for Recipient URL and Destination URL' option checked. - Audience URI (SP Entity ID):
https://YOUR_BOARD.nolt.ioLeave the other fields in its default status. The configuration should look similar to the screenshot below:
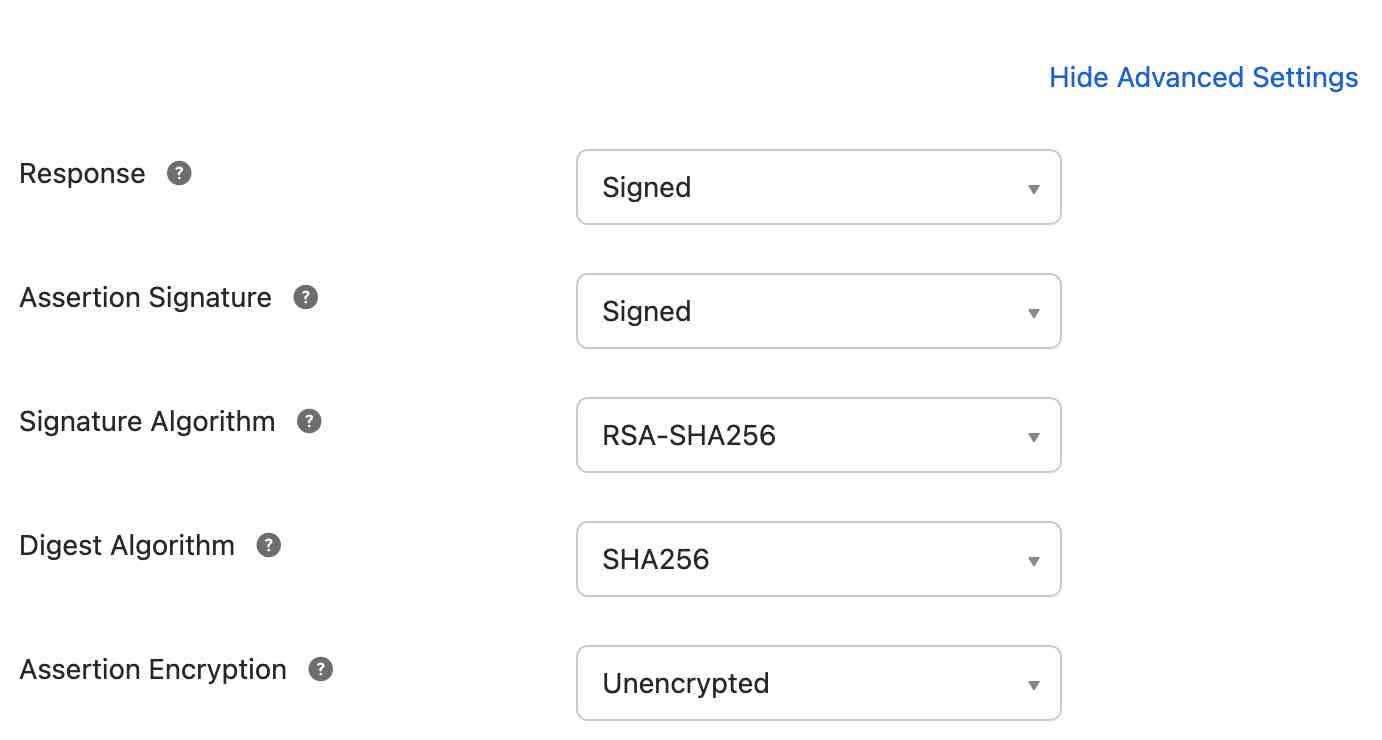
- Select Show Advanced SettingsVerify that Assertion Signature is Signed, Signature Algorithm is RSA-SHA256 and Digest Algorithmis SHA256.
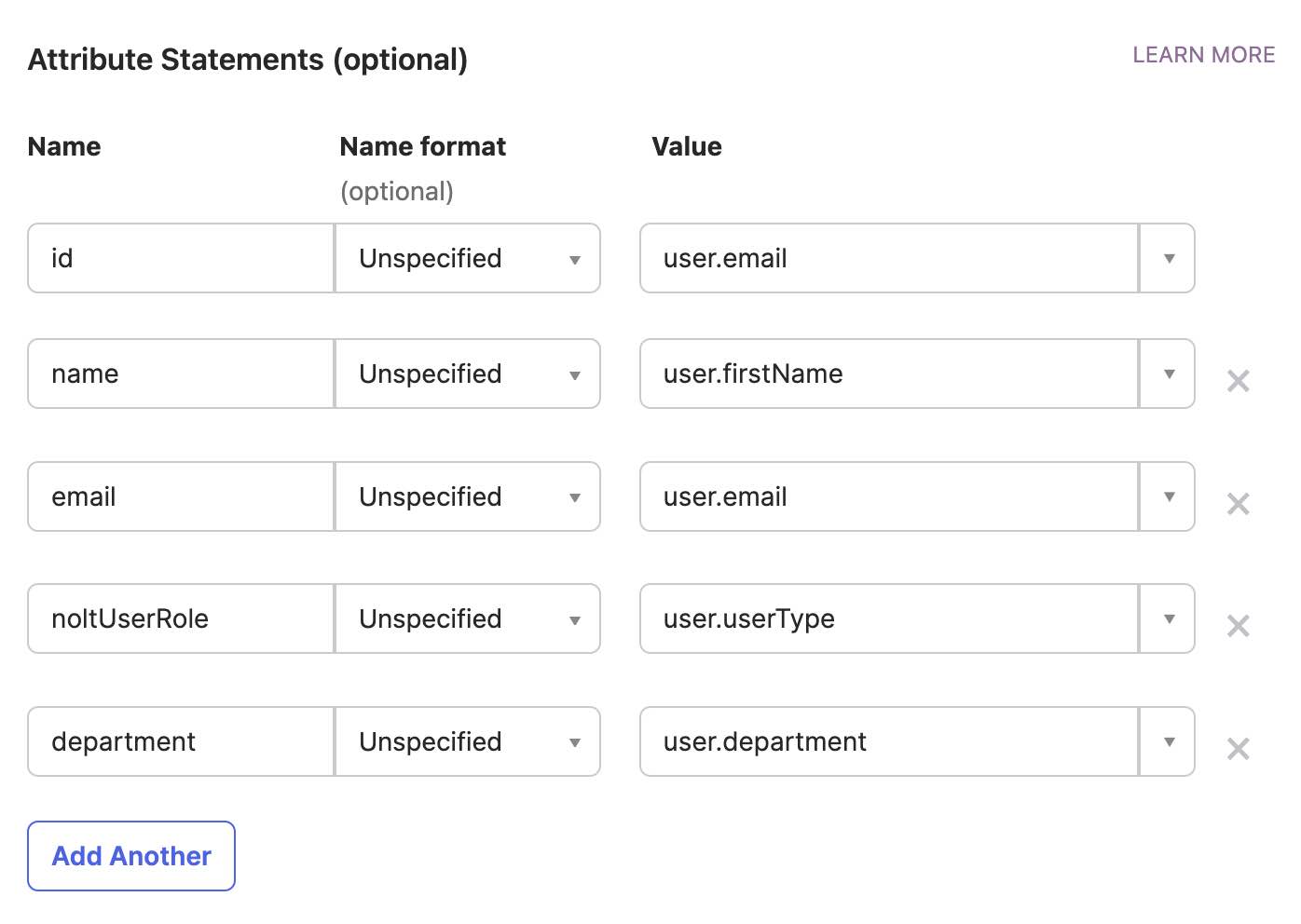
- Attribute StatementsIt's mandatory to pass the below fields with the same field-name mentioned below (case sensitive).
- idLeave the name format to Unspecified and value to your preferred id field (can be email)
- nameLeave the name format to Unspecified and value to user.firstName
- emailLeave the name format to Unspecified and value to user.email
- noltUserRole (Optional)Leave the name format to Unspecified and value to user.ROLE_FIELD (Must be one of ADMIN/MODERATOR case-sensitive)
- Custom Attributes (Optional)You can set the custom attributes that will be shown in the user profile. You can use any field-name and field value for custom attributes.
The id should be unique for every user. The field picture (optional) can also be passed. - id
- Select 'I'm a software vendor...' and click finish.This sets up the application in Okta to be integrated with Nolt. The users should be added to this application from your directory. Open the SAML setup instructions (available at right hand corner) for the application.
3. Integrating in Nolt
Navigate to your board → Integrations → SAML 2.0. Set up all the required fields to activate the integration.
- IDP entity ID (Issuer URL):Copy the Identity Provider Issuer from the Okta SAML setup instructions. It will be similar to the below format.
http://www.okta.com/SOME_KEY - SP Entity ID (Audience URI):
https://YOUR_BOARD.nolt.io - X509 Certificate:Copy the X.509 certificate from the Okta SAML setup instructions.
- Remote Login URL:Copy the Identity Provider Single Sign-On URL from the Okta SAML setup instructions.
- Remote logout URL (optional)Add a Remote logout URL if you want to redirect users to a specific URL after they log out from their Nolt account.
- User role structure (optional)If you are passing the user role for nolt other than noltUserRole from the attribute statement, you need to set up this field. If you have setup the attribute statement as follows:Then the user role structure should be set as follows:
userRole: 'ADMIN'userRole - Custom Attributes (optional)If you have set any custom attributes in the attribute statement, you need to set up this field. If you have setup the attribute statement as follows:Then the user custom attribute structure should be set as follows:
department empId{"Department":"department","EmployeeID":"empId"} - Click Test and activate:This should activate the SSO. To test the SSO try logging in as a new user.
Need help?
Please feel free to reach out at hello@nolt.io for any help regarding SSO.
Related
Setting up SSO with OpenID Connect (OIDC)
Setup OpenID Connect via your IdP to provide single-sign-on.
Setting up SSO with SAML 2.0
Setup SAML via your IdP to provide single-sign-on.
Setting up SSO with Auth0
Setup single-sign-on (SSO) via Auth0.
Setting up SSO with Microsoft Entra ID (Azure AD)
Setup single-sign-on (SSO) via Microsoft Entra ID.
Setting up SSO with OneLogin
Setup single-sign-on (SSO) via OneLogin.